Zero Trust in Azure: No trust is maximum security
Remove all trust and verify EVERYTHING might sound like a harsh and oppressive principle if we were talking about values in a family or a relationship. But when it comes to developing IT applications, it’s fundamental to ensuring that all systems and data remain protected against modern cyber threats. Instead of relying on implicit assumptions about what is safe, Zero Trust is built on the principle that all access—whether from inside or outside—must be verified. This prevents unnecessary access to critical resources, even for those we trust. If you trust everyone, you can trust no one.
The Zero Trust principle eliminates all implicit trust from digital infrastructure.
Security is not something we add as an afterthought to a project – it’s an integral part of everything we build from the start. By designing cloud-native applications with Zero Trust as the foundation, we create solutions which are robust, flexible, and protected against modern cyber threats. Zero Trust means that no one is trusted by default, whether they are inside or outside the network. By implementing it correctly in Azure, organizations can achieve a secure and efficient infrastructure.
Core Principles of Zero Trust
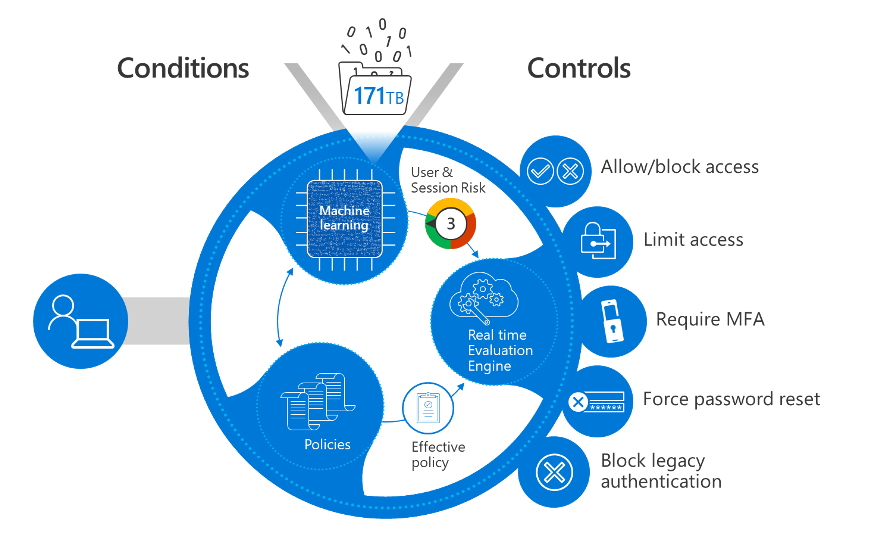
Zero Trust rests on three key principles: All access must be explicitly verified, trust must be minimized, and systems should be designed with the assumption that breaches can occur. This means that users, devices, and applications must always be validated, and strict access controls must be implemented.
Summary:
Always verify users and devices before granting access
Minimize implicit trust in networks and systems
Design with the assumption that security breaches may happen